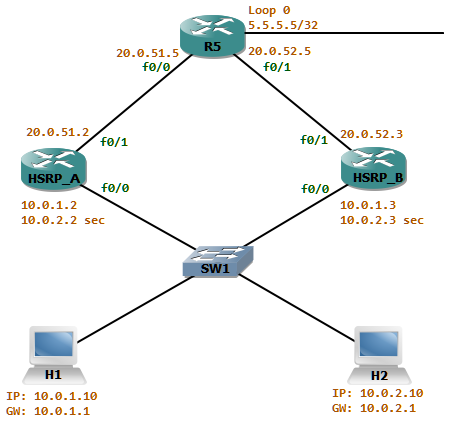
Initially there were about 250 hosts in the network attached to switch SW1. The Gateway router HSRP_A is the active router for the network. As the number of hosts increased in the network attached to SW1, a new subnet (10.0.2/24) is introduced as a secondary address in the gateway routers. To achieve some load sharing HSRP_B will be the active router for the group 1 for the network 10.0.1/24 and HSRP_A active for the group 2 which is the 10.0.2/24 network.
The ospf cost advertised from HSRP_A is better than the one advertised from HSRP_B. Thus the return traffic from the network attached to R5 will always take the path via HSRP_A. now let’s look at this scenario where some traffic filtering is in place.
HSRP_A has a filtering rule which states only to allow inbound TCP sessions if it was originated from the networks attached to SW1. For this HSRP_A has an outbound access-list attached to f0/1 named OUTBOUND_ACL_OUT which reflects the outgoing tcp sessions to a reflexive access-list named TCP.
ip access-list extended OUTBOUND_ACL_OUT
permit ospf any any
permit icmp any any
permit tcp any any reflect TCPinterface FastEthernet0/1
ip access-group OUTBOUND_ACL_OUT outThe packets inbound to interface f0/1 is evaluated against the reflected access-list TCP.
ip access-list extended OUTBOUND_ACL_IN
evaluate TCP
permit ospf any any
permit icmp any anyinterface FastEthernet0/1
ip access-group OUTBOUND_ACL_IN in
With this configuration let us check the problem with asynchronous routing. First HSRP_A will be the active router for both groups. This means we do not have any asynchronous routing.
HSRP_A#sh standby brief
P indicates configured to preempt.
|
Interface Grp Pri P State Active Standby Virtual IP
Fa0/0 1 120 P Active local 10.0.1.3 10.0.1.1
Fa0/0 2 120 P Active local 10.0.1.3 10.0.2.1
Let us look the way packets route in the network. we can use the extended ping to record the route the packet takes.
H1#ping
Protocol [ip]:
Target IP address: 5.5.5.5
Repeat count [5]: 1
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: yes
Source address or interface:
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]: r
Number of hops [ 9 ]:
Loose, Strict, Record, Timestamp, Verbose[RV]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 1, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds:
Packet has IP options: Total option bytes= 39, padded length=40
Record route: <*>
(0.0.0.0)
(0.0.0.0)
(0.0.0.0)
(0.0.0.0)
(0.0.0.0)
(0.0.0.0)
(0.0.0.0)
(0.0.0.0)
(0.0.0.0)
Reply to request 0 (76 ms). Received packet has options
Total option bytes= 40, padded length=40
Record route:
(10.0.1.10) !exit interface IP of H1 towards 5.5.5.5
(20.0.51.2) !exit interface IP of HSRP_A towards 5.5.5.5
(5.5.5.5)
(20.0.51.5) !exit interface IP of R5 towards 10.0.1.10
(10.0.1.2) !exit interface IP of HSRP_A towards 10.0.1.10
(10.0.1.10) <*>
(0.0.0.0)
(0.0.0.0)
(0.0.0.0)
End of list
Success rate is 100 percent (1/1), round-trip min/avg/max = 76/76/76 ms
H1#
As expected the goes to HSRP_A which is the active router. It uses it’s exit interface which has the IP 20.0.51.2. Finally the packet arrives at R5. It the routes back to HSRP_A as it advertices a better ospf cost. The same will be for H2 as HSRP_A is active for both groups.
Let us make HSRP_B the active router for the 10.0.1/24 network
HSRP_B(config)#interface f0/0
HSRP_B(config-if)#standby 1 priority 150
*Mar 2 00:03:49.778: %HSRP-5-STATECHANGE: FastEthernet0/0 Grp 1 state Standby -> Active
H1#ping
Protocol [ip]:
Target IP address: 5.5.5.5
Repeat count [5]: 1
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: yes
Source address or interface:
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]: r
Number of hops [ 9 ]:
Loose, Strict, Record, Timestamp, Verbose[RV]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 1, 100-byte ICMP Echos to 5.5.5.5, timeout is 2 seconds:
Packet has IP options: Total option bytes= 39, padded length=40
Record route: <*>
(0.0.0.0)
(0.0.0.0)
(0.0.0.0)
(0.0.0.0)
(0.0.0.0)
(0.0.0.0)
(0.0.0.0)
(0.0.0.0)
(0.0.0.0)
Reply to request 0 (84 ms). Received packet has options
Total option bytes= 40, padded length=40
Record route:
(10.0.1.10)
(20.0.52.3)
(5.5.5.5)
(20.0.51.5)
(10.0.1.2)
(10.0.1.10) <*>
(0.0.0.0)
(0.0.0.0)
(0.0.0.0)
End of list
Success rate is 100 percent (1/1), round-trip min/avg/max = 84/84/84 ms
H1#
Now we can see that the packet transverses via HSRP_B and comes back via HSRP_A. With the filtering in place as HSRP_A does not create a reflective tcp session entry, it will deny the inbound tcp packet from R5. We can see this if we debug ip icmp in R5 while telneting from H1.
R5#
*Mar 2 00:08:10.306: ICMP: dst (5.5.5.5) administratively prohibited unreachable rcv from 20.0.51.2
But the telnet from H2 will succeed as the outgoing packet takes the path via HSRP_A.
H2#telnet 5.5.5.5
Trying 5.5.5.5 ... Open
R5>
HSRP_A#sh access-list TCP
Reflexive IP access list TCP
permit tcp host 5.5.5.5 eq telnet host 10.0.2.10 eq 50962 (15 matches) (time left 297)
HSRP_A#
We can see that HSRP_A does have a dynamic entry for the tcp session originated from H2.
To solve this problem, we could use another physical interface for the second network. Thus each HSRP group will have its own interface.